
Hey mates , today we're going to continue our previous topic and this will be the last part :) .
In the beginning , we've seen before how we succeed to hack the server by an SQLi vulnerability , we've pulled all the necessary data that we needs to hack the website , now turn to gain a shell into the server , am i right ?!!
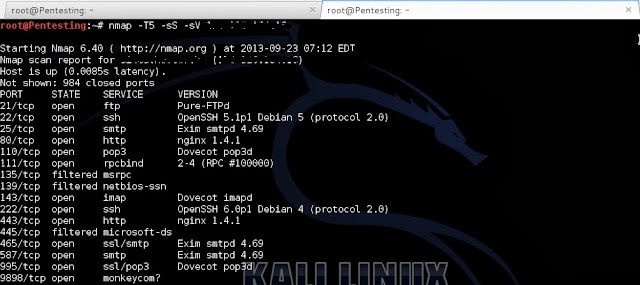
Now lets do a port scan using nmap :
These are the services that we founded already opened .
As a pentester , usually you will think about fuzzing one of the services depends on it if it could be able to fuzz or not , and certainly you will be looking for a vuln service .
Thats right , but you don't need to spend time just downloading the services on your machine and doing a fuzz stuff , this aspect just for the exploit researcher , i mean you could do it but it could take sometime and finally we need a feasible pentest work .
Lets see first " Pure-Ftpd " service if it exploitable or not especially the version is not determined .
Always there is something came to rescue and exploitdb tool of course the most appropriate for this mission :) :
Always there is something came to rescue and exploitdb tool of course the most appropriate for this mission :) :

We can't use this Poc becuase its not a command execution bug its a crash , dos attack and we need something to give us a remote shell , lets see something else this time is OpenSSH 5.1p1 Debian 5 , interesting since it gives us the version and the ssh protocol " 2.0 " :

No one is valid for exploiting :( .
We still have a chance , lets try the 3rd service " Exim smtpd 4.69 " :

Woww ! , we are lucky , the same version of the service and the exploit is ruby-based , so definitely it's part of Metasploit project , lets give that a try :

Two different exploits , first one is command execution and its in this year has been uploaded , whereas the 2nd exploit is heap-based buffer overflow and it's old somewhat but its a Unix-based exploit despite , it still in computation because its at the same version of our current service , lets fill out the options and exploit :
Everything is completely in it position , lets type exploit and see what will happen :
Very sad :( , the exploit doesn't seem to work , it says the address in Unrouteable , and i think it needs a locally machine to be exploitable .
Never mind lets try the second exploit , as always lets fill the options , exploits and watch the results :

Hm! , it seems not prone to be exploitable , thus , for the rests of the services , but now is the most interesting part of this topic just give me your concentrate :) .
take a look at the end of the scan :
9898 tcp port is open and associated with Monkeycom service , it's a software port that used to exchange data directly instead of going through a file or other temporary storage location , and to exchange files also between computers through the internet , somehow its a defunct protocol these days because i've never seen any server ran this port before , many are saying that this is a warning to find this port open in your internal network , if you want to check your machine if it contain this service or there another service that using this port just type into your terminal " lsof | grep 9898 " , any way , lets see whats behind this port by metasploit it might be holding any exploit for this service :
Meta gives nothing , lets see exploitdb tool :

also exploitdb gives nothing , what is suppose to do ? ........ ?)
Lets associate the port with the link as the following :
x.x.x.x:9898
and see the output :
OMGG ! , are you kidding me , bit me , i think its just a dream ???? , yes yes that's real you are not dreaming , simplicity , isn't it ?? .
It listed all the system files and folders , ( etc , var , home , logs , root .. etc ) , we've done a great render , what else you want more than this ;) !!! .
Evidently , its a big success , i told you before always should have been a chance do not surrender .
Now , lets go back a bit , we've already hacked a website inside the server , haven't we ? , precisely , we still have a target which is a university website we agreed on this point , so , all we want is a shell session , this image for the hacked website :

Very satisfying , but don't forget , we can't declare our fully controling , we are still not able to execute , delete , copy , or even any privileges at all , we can just reading , navigating exactly like file disclosure vulnerability or directory traversal .
If you itched your head a little , you will recognize the following :
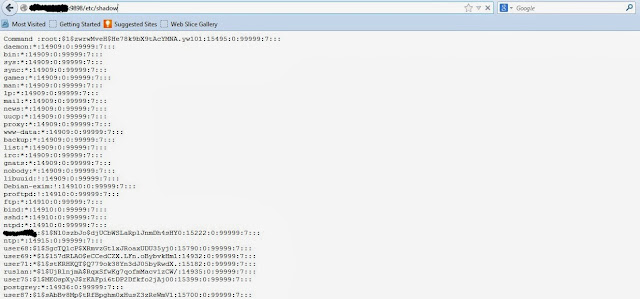
etc/passwd
etc/shadow
are available for reading , lets see :
nothing yet happened , with all eagerness you want to crack the root hash and just login by putty , but wait the two important files are between our hands , why we shouldn't try to unshadow them ?? , shall we !! ??? .
Ok , first , select all and copy both files content and past them separately in two different files one for shadow and two for passwd , then type as the following :
Now we are ready , the proof of concept is we want to put each user with it hash and to crack them all at the same time , you have to wait from 1 minute to 2 hours or maybe more , just check them from time to time by using this command :
At this moment john will try as much as possible to crack each user hash , lets see the result :
Splendid :) , the first two divided sections are the username and the password , I've tried them all , just one was available , the distinct user " lexx8881 " .
Now the last step , lets login typing the following command into terminal :
ssh lexx8881@x.x.x.x <------ the ip of the server
Voilaaaaa :-) , we made it .
So guys , hope these series gained your satisfaction and was a useful tutorial and assisted your needs especially this tutorial is recently being reported to the company .
See you next time , have a great day ahead , try harder , and more to come ;) .
Follow me ;) , http://t.co/LKiDzHzjdk
— Reznov (@pentester11) October 3, 2013









Comments
Post a Comment